Review attack surface on Telegram example
It’s been a while since I wrote something here… Let’s dig an iceberg of “security in general” again.
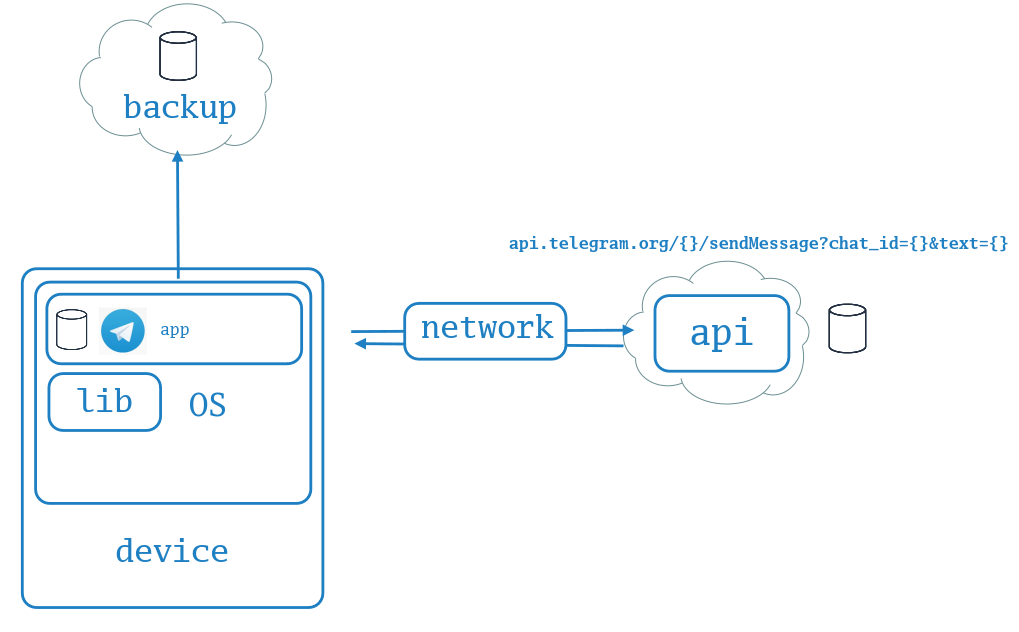
This is a very brief review that is using Telegram mobile application, which connects through the mobile network to a remote server, just as an example. The attack surface may be different for you, but it can still contain the same basic elements (not always).
- Application layer (Telegram app)
- Libraries
- OS + backups
- Device + GSM stack
- Network layers
- API service + some backend
- Third-party services
attack in a real-case scenario⌗
There are a lot of theoretical directions, but, most likely, an attack scenario will be selected based on:
- Complexity (physical access) - it must be as low as possible;
- Low cost;
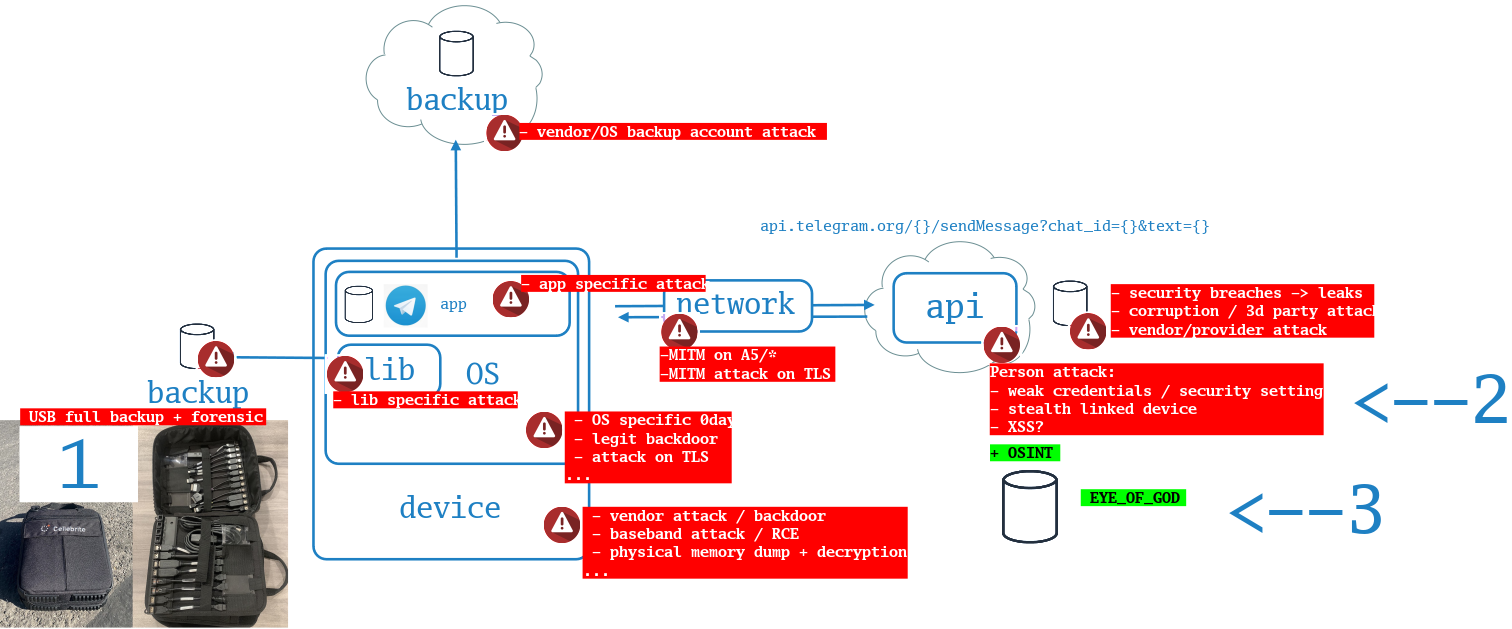
most likely…⌗
- Attack by performing physical backup and forensic tools on the dump ( CelleBrite, etc );
- Attack on your account (SIM clone, linked hidden device, legit C2 backdoor implant, etc.);
- Collecting data about you using open source (OSINT);
Other methods are also available, but the cost will increase, which means they are less likely will be used. 💰
Remediation⌗
TL;DR:
- Use a trustworthy vendor with their security department and install all security patches (updates);
- Use a password manager with a strong master password;
- Enable MFA, not on a mobile phone if possible;
- Don’t do anything stupid, such as clicking on suspicious links or posting your personal data in public chat, public profile, etc.
- If this is not what you do for a living, hire(ask) someone experienced enough to consult you - on how to protect according to your threat model; May be double check this with some other expert;

This is all.
But…
If this is not enough for you… :)
:: Before you start⌗

- There is no such thing as “absolute security”;
- Not a point to be reached. It’s a vector to be followed.
- Security is always in context according to your threat model
- Your threat model, most likely, is not my threat model;
- This is not the guide, but just some hints;
- Don’t do anything illegal; Most likely you will be caught;

:: Backups - make them exist and be secure⌗
- Make backups of your critical data;
- Test your backups - how they can be recovered;
- Test them again, from time to time. Recovery of damaged encrypted data can be much harder than you may think;
- Keep backups in a secure, trusted location (more than one);
- Make backups always encrypted with strong encryption and a strong passphrase;
- Store on physical media in a secure location only part of the modified decryption key for backup for recovery, as a hint to recreate the original key;
- Backup volumes should not be available from the target system for listing (no mounted backup volumes, or available for writing AWs S3 buckets);
This is a bad idea:
root@some-serer-123 $ ls -lah /mnt/backups
... listing backups ...
In this case, a compromised server can be used to destroy the data and backups simultaneously.
:: Devices :: use trustworthy⌗
- Avoid using backdoored, corporate hardware for any personal task; button phones backdoors(rus)
- Avoid installing any third-party untrusted software;
- Avoid giving your physical device to anyone, even for a short period;
- If your device has been stolen and returned - perform “Reset to factory settings”
- Reset to factory settings can help, and in some cases - can’t. Just copy the data and forget about this device;
- Avoid plugging in your device in an unknown system or charging port and or using an unknown charging cable;
- Use separate devices, virtual machines, and networks for different activities (if possible)
- Avoid using “compromised” by hardware vulnerabilities devices;

:: Security patches :: Install them⌗
- Enable and always install all security patches for your OS and apps;
- If there is some software “X” which is not supported by the relevant OS version or works slowly - consider buying a separate network-isolated device just for running this “X” unsupported software (or use it in a virtual machine, if possible);
- Consider using Security focused OS:
- GrapheneOS as smartphone Android replacement;
- Qubes or Subgraph as desktop
- Tails as a Read-only LIVE OS
- or just use regular OpenBSD, DragonflyBSD, or GNU/Linux if you know what you are doing :)
:: Passwords :: use Password Manager⌗
- Use a password manager (such as keepassxc) to generate strong passwords
- Use different passwords for each system
- Avoid using your personal data, phone number, date of birth, name of family members, pets, etc.
- Dictionary words should be avoided (such as @apple123)
- Avoid common keyboard sequences (such as “qwerty”)
These are all bad passwords:
!QAZ2wsx#EDC4rfv
mysecretpassword0*
7ujMko0admin
7ujMko0vizxv
LFL870206
5172980a
north33
1terry
11moneys
34babie
edward59
teamochapa
24a.24a
44--------44
1234567890
000---11
8688851a
1100a
8688851

:: Account recovery :: Check your recovery⌗
- Check account recovery - how you will recover your account without knowing your password;
- Set the actual password instead of answering “Your pet name”. Answer “WHwiWHI0-1@%%” may be a good pet name.
- Keep answers for your secret questions in a secure place;

:: Password manager :: master password⌗
- Set a strong master password for a password manager
- Keep a paper copy(?) of part of the password to recall it when you forget it;
- You can encrypt or modify the master password stored on a physical copy or store it in a big bunch of garbage;

:: Passwords - compromised⌗
- Check your accounts logins for being compromised ( Example: https://haveibeenpwned.com/ ). If it was detected leaked database with your e-mail in it
:: Linked devices⌗
- Inspect all of your linked devices for your account;
- Disable unused(or lost) linked devices;
- Check for active sessions - reset your password if you see any anomalous activity;
:: Two-factor authentication⌗
- Enable two-factor authentication;
- If feasible, use a different device for the second factor;
- GSM mobile number is a bad idea for recovery or second factor as SIM card can be cloned;

:: Don’t use VPN for security⌗
- As it was said multiple times - VPN can protect from some vectors, but, most likely, you making things worse by letting someone to monitor your activity or perform direct connections to your devices on opened ports;
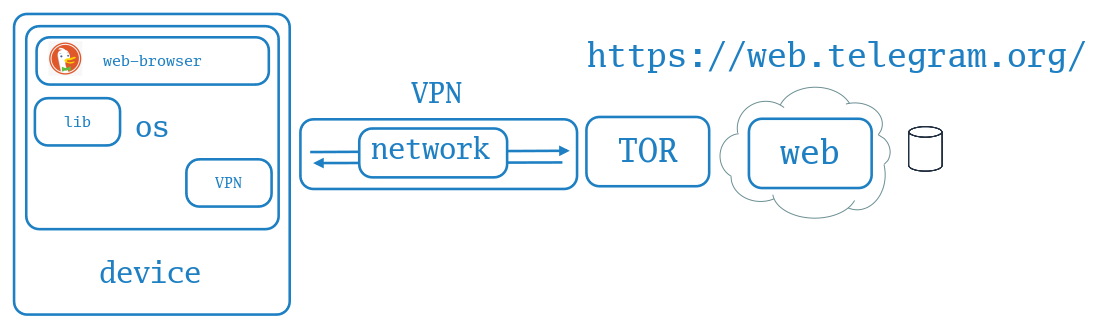
:: Web application instead of installed⌗
- Using web application instead of installed app can reduce attack surface;
:: Ending :: Conclusion ::⌗
Just go outside to the forest (or Park or etc) and breathe in with some fresh air. When you walk through trees, think about the worst-case scenario.
For my opinion, if you have found yourself as a person who need to know about information security to protect your physical life - it is something terribly wrong is going on (unless you are a spy :) ). May be the problem can be solved using different method, not using information security best practices, by relocation to another country.

One more thing… To protect the information, when you don’t have enough resources, there are two more ways:
- Destroy it and never tell anyone(if this is available);
- Make it public;
Just remove yourself from the equation; Before you do anything - think about the consequences twice.

Thank you for reading. Have a nice day ^__^